In cities across Russia, large boxes in locked rooms are directly connected to the networks of some of the country’s largest phone and internet companies.
These unsuspecting boxes, some the size of a washing machine, house equipment that gives the Russian security services access to the calls and messages of millions of citizens. This government surveillance system remains largely shrouded in secrecy, even though phone and web companies operating in Russia are forced by law to install these large devices on their networks.
But documents seen by TechCrunch offer new insight into the scope and scale of the Russian surveillance system — known as SORM (Russian: COPM) — and how Russian authorities gain access to the calls, messages and data of customers of the country’s largest phone provider, Mobile TeleSystems (MTS).
The documents were found on an unprotected backup drive owned by an employee of Nokia Networks (formerly Nokia Siemens Networks), which through a decade-long relationship maintains and upgrades MTS’s network — and ensures its compliance with SORM.
Chris Vickery, director of cyber risk research at security firm UpGuard, found the exposed files and reported the security lapse to Nokia. In a report out Wednesday, UpGuard said Nokia secured the exposed drive four days later.
“A current employee connected a USB drive that contained old work documents to his home computer,” said Nokia spokesperson Katja Antila in a statement. “Due to a configuration mistake, his PC and the USB drive connected to it was accessible from the internet without authentication.”
“After this came to our attention, we contacted the employee and the machine was disconnected and brought to Nokia,” the spokesperson said.
Nokia said its investigation is ongoing.
‘Lawful intercept’
The exposed data — close to 2 terabytes in size — contain mostly internal Nokia files.
But a portion of the documents seen by TechCrunch reveals Nokia’s involvement in providing “lawful intercept” capabilities to phone and internet providers, which Russia mandates by law.
SORM, an acronym for “system for operative investigative activities,” was first developed in 1995 as a lawful intercept system to allow the Federal Security Services (FSB, formerly the KGB) to access telecoms data, including call logs and content of Russians. Changes to the law over the last decade saw the government’s surveillance powers expand to internet providers and web companies, which were compelled to install SORM equipment to allow the interception of web traffic and emails. Tech companies, including messaging apps like Telegram, also have to comply with the law. The state internet regulator, Roskomnadzor, has fined several companies for not installing SORM equipment.
Since the system’s expansion in recent years, several government agencies and police departments can now access citizens’ private data with SORM.
Most countries, including the U.S. and the U.K., have laws to force telecom operators to install lawful intercept equipment so security services can access phone records in compliance with local laws. That’s enabled an entirely new industry of tech companies, primarily network equipment providers like Nokia, to build and install technologies on telecom networks that facilitate lawful intercepts.
Alexander Isavnin, an expert at Roskomsvoboda and the Internet Protection Society, told TechCrunch that work related to SORM, however, is “classified” and requires engineers to obtain special certifications for work. He added that it’s not uncommon for the FSB to demand telecom and internet companies buy and use SORM equipment from a pre-approved company of its choosing.
The documents show that between 2016 and 2017, Nokia planned and proposed changes to MTS’s network as part of the telecom giant’s “modernization” effort.
Nokia planned to improve a number of local MTS-owned phone exchanges in several Russian cities — including Belgorod, Kursk and Voronezh — to comply with the latest changes to the country’s surveillance laws.
TechCrunch reviewed the documents, which included several floor plans and network diagrams for the local exchanges. The documents also show that the installed SORM device on each phone network has direct access to the data that passes through each phone exchange, including calls, messages and data.
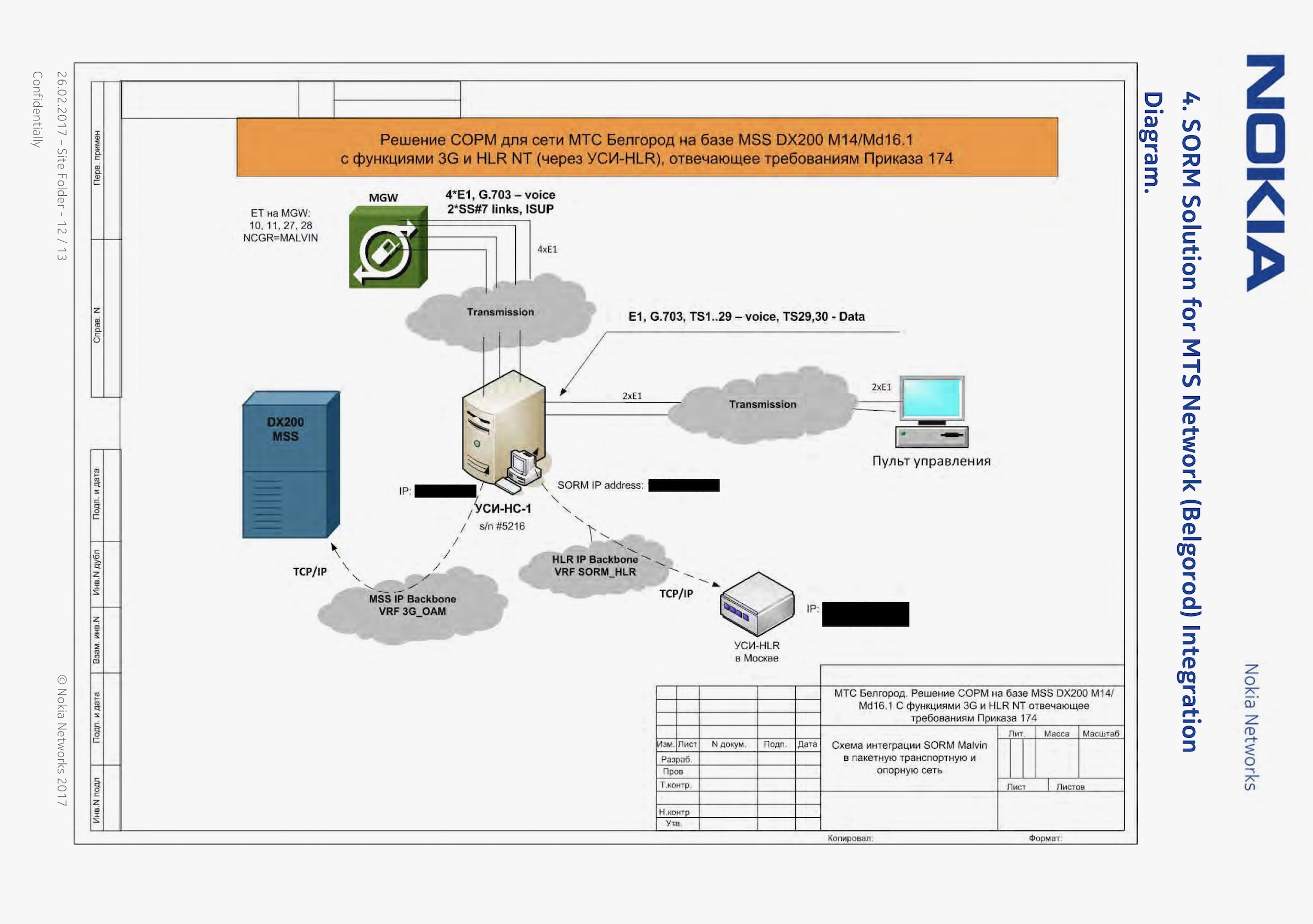
MTS’ exchange in Belgorod containing SORM equipment. Authorities can remotely access the system.
The plans contain the physical address — including floor number — of each phone exchange, as well as the location of each locked room with SORM equipment in large bold red font, labeled “COPM.” One document was titled “COPM equipment installation [at] MTS’ mobile switching center,” a core function for handling calls on a cell network.
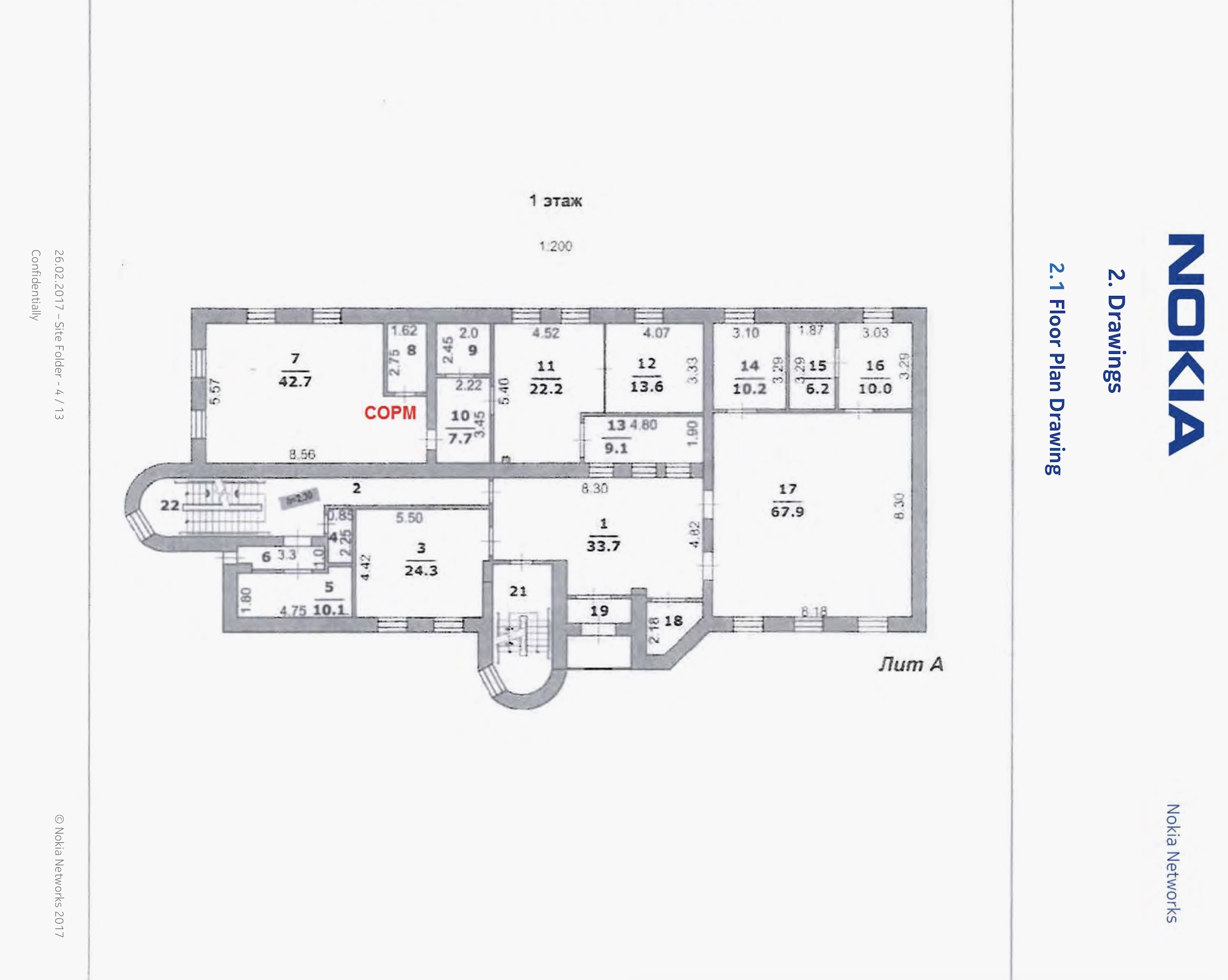
An unedited floor plan detailing where the SORM equipment is located.
One photo showed the inside of one of the SORM rooms, containing the sealed box containing intercept equipment with the letters “COPM” in large font on the metal cabinet next to an air-conditioning unit to keep the equipment cool.

A photo of a SORM (COPM) device in a locked room at one of MTS’ local phone exchanges.
Nokia says it provides — and its engineers install — the “port” in the network to allow lawful intercept equipment to plug in and intercept data pursuant to a court order, but denied storing, analyzing or processing intercepted data.
That’s where other companies come into play. Russian lawful intercept equipment maker Malvin Systems provides SORM-compatible technology that sits on top of the “port” created by Nokia. That compatible technology allows the collection and storage of citizens’ data.
“As it is a standard requirement for lawful interception in Russia and SORM providers must be approved by the appropriate authorities, we work with other companies to enable SORM capabilities in the networks that we provide,” said Nokia’s spokesperson, who confirmed Malvin as one of those companies.
Nokia’s logo was on Malvin’s website at the time of writing. A representative for Malvin did not return a request for comment.
Another set of documents shows that the “modernized” SORM capabilities on MTS’s network also allows the government access to the telecom’s home location register (HLR) database, which contains records on each subscriber allowed to use the cell network, including their international mobile subscriber identity (IMSI) and SIM card details.
The documents also make reference to Signalling System 7 (SS7), a protocol critical to allowing cell networks to establish and route calls and text messages. The protocol has widely been shown not to be secure and has led to hacking.
MTS spokesperson Elena Kokhanovskaya did not respond to several emails requesting comment.
‘Bulk wiretapping’
Lawful intercept, as its name suggests, allows a government to lawfully acquire data for investigations and countering terrorism.
But as much as it’s recognized that it’s necessary and obligatory in most Western countries — including the U.S. — some have expressed concern at how Russia rolled out and interprets its lawful intercept powers.
Russia has long faced allegations of human rights abuses. In recent years, the Kremlin has cracked down on companies that don’t store citizens’ data within its borders — in some cases actively blocking Western companies like LinkedIn for failing to comply. The country also has limited freedom of speech, expression and dissidents, and activists are often arrested for speaking out.
“The companies will always say that with lawful interception, they’re complying with the rule of law,” said Adrian Shahbaz, research director for technology and democracy at Freedom House, a civil liberties and rights watchdog. “But it’s clear when you look at how Russian authorities are using this type of apparatus that it goes far beyond what is normal in a democratic society.”
For Nokia’s part, it says its lawful intercept technology allows telecom companies — like MTS — to “respond to interception requests on targeted individuals received from the legal authority through functionality in our solutions.”
But critics say Russia’s surveillance program is flawed and puts citizens at risk.
“In Russia, the operator installs it and have no control over what is being wiretapped Only the FSB knows what they collect.”
Alexander Isavnin, expert
Isavnin, who reviewed and translated some of the files TechCrunch has seen, said Russia’s view of lawful intercept goes far beyond other Western nations with similar laws. He described SORM as “bulk wiretapping.”
He said in the U.S., the Communications Assistance for Law Enforcement Act (CALEA) requires a company to verify the validity of a wiretap order. “In Russia, the operator installs it and have no control over what is being wiretapped,” he said. The law states that the telecom operation is “not able to determine what data is being wiretapped,” he said.
“Only the FSB knows what they collect,” he said. “There is no third-party scrutiny.
Nokia denied wrongdoing, and said it is “committed” to supporting human rights.
Nokia chief marketing officer David French told TechCrunch in a call that Nokia uses a list of countries that are considered “high-risk” on human rights before it sells equipment that could be used for surveillance.
“When we see a match between a technology that we think has potential risk and a country that has potential risk, we have a process where we review it internally and decide to go forward with the sale,” said French.
When pressed, French declined to say whether Russia was on that list. He added that any equipment that Nokia provides to MTS is covered under non-disclosure agreements.
A spokesperson for the Russian consulate in New York could not be reached by phone prior to publication.
This latest security lapse is the second involving SORM in recent months. In August, a developer found thousands of names, numbers, addresses and geolocations said to have leaked from SORM devices. Using open-source tools, Russian developer Leonid Evdokimov found dozens of “suspicious packet sniffers” in the networks of several Russian internet providers.
It took more than a year for the internet providers to patch those systems.
Ingrid Lunden contributed translations and reporting.
Got a tip? You can send tips securely over Signal and WhatsApp to +1 646-755-8849. You can also send PGP email with the fingerprint: 4D0E 92F2 E36A EC51 DAAE 5D97 CB8C 15FA EB6C EEA5.
